Access control and security entrance integration is a specialized discipline. Sure, security entrances require only a dry contact and can integrate with virtually any access control system, but there are some things you should consider when you’re looking into the right access control system for your organization’s security goals.
A great person to talk to about security entrances and integration is our own Kurt Measom, Vice President of Technology & Product Support. With 21 years of experience in the security industry - four of those years serving as an advisor for security solutions to dozens of Fortune 1000 companies – and a Lenel certification, Kurt has extensive knowledge of all things access control and has “seen it all.”
I caught him in the hallway the other day and asked him about the most common mistakes he has witnessed. Here are three mistakes that he’s seen a number of times that we hope to help you avoid.
Mistake 1: Device placement
Q: Before we talk about mistakes you’ve seen in device placement, why would you say the placement of a device is important?
K: The placement of your access control device will not only effect the throughput of your entrance, but also its level of security or effectiveness at tailgating mitigation. If you’re spending a significant amount of money on physical security entrances, you’ll probably want to know if your access control device is negatively impacting the entrance’s ability to provide the intended level of security.
Q: Absolutely. So what types of placement mistakes have you seen where throughput and security were impacted?
 K: (1) Believe it or not, placement of a device on a wall to the left side of the entrance vs. the right. Let me explain… the majority of the world drives on the right side of the road. That is most intuitive for users, and that is why authorized users enter our security revolving doors to the right. With this in mind, I’ve seen companies place the access control device on the LEFT side of a hallway, opposite of the entry point of the door.
K: (1) Believe it or not, placement of a device on a wall to the left side of the entrance vs. the right. Let me explain… the majority of the world drives on the right side of the road. That is most intuitive for users, and that is why authorized users enter our security revolving doors to the right. With this in mind, I’ve seen companies place the access control device on the LEFT side of a hallway, opposite of the entry point of the door.
Here is an example: It is lunchtime. Many people are coming and going through a security revolving door. There is a large group of people exiting the door while I am trying to enter. I have to cross through oncoming traffic to get to the card reader on the left side of the hallway, scan my badge, and then maneuver through traffic to get back to the entrance of the door on the right side. This is not an ideal set up for efficient throughput, as you can imagine. There is also the chance that while I’m trying to make my way through traffic after authorization, someone else could jump into the door and make it through. What if that “someone else” was a person intent on doing harm?
(2) Distance of the device from the entrance. Let’s stick with the picture we have in our minds of the security revolving door in the hallway. The access control device is mounted on the right side of the hallway, BUT the device is 10 feet from the entrance of the door. That’s a lapse of several seconds between the access control device and the security entrance. During a busy time of day, like lunch, someone could march straight past the person that just authorized and enter through the door. Again, if this isn’t someone with credentials, you could have a serious problem on your hands.
Mistake 2: Speed of activation is too high
Q: Can an access control device really work too quickly to be effective?
K: Yes. Actually, the faster the access control device, the higher probability of a false acceptance, or the device saying that someone is authorized when they really aren’t. When you think about it simply, anytime that we as humans try to do something faster and faster, quality tends to dip. The same is true of an access control device. There is a biometric device technology on the market that only requires a person to wave their hand through for authentication – no more actually placing your hand on the device for its geometry to be verified. While this significantly increases the throughput of the entrance, there is a greater probability of the device saying someone is authorized when they really aren’t. Are you willing to take that risk?
Q: What is your take on “verification on the fly” systems and their impact on security and speed?
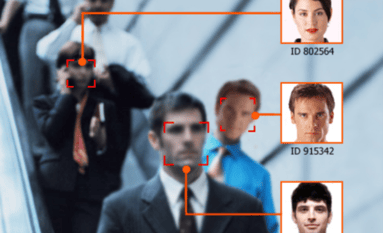 K: So a “verification on the fly” system recognizes facial features as a person is walking up to the device. Manufacturers of these devices tout that their technology can recognize a specific face among a crowd from 15 feet away or more. While this is great technology, it isn’t really taking off because there is much room for error. To achieve the activation speed advertised, you’d be risking a higher level of false acceptance. Also, if three people approach and one is authorized the entrance will unlock, but who is actually entering?
K: So a “verification on the fly” system recognizes facial features as a person is walking up to the device. Manufacturers of these devices tout that their technology can recognize a specific face among a crowd from 15 feet away or more. While this is great technology, it isn’t really taking off because there is much room for error. To achieve the activation speed advertised, you’d be risking a higher level of false acceptance. Also, if three people approach and one is authorized the entrance will unlock, but who is actually entering?
The best way to ensure the right person passes through the entrance is to use two-factor authentication. You could have the facial recognition device to start with, but you’d need to add a secondary reader right at the door to confirm that the same, authorized user is the one getting in.
Mistake 3: Not intuitive for users
Q: What pitfalls in intuitive use have you seen in your experience?
K: There are two areas: sophisticated devices and hidden placement.
(1) Is the access control device something that your employees will know how to use intuitively, like a card swipe reader? Or is it something that will require training, like an iris scanner or BLE reader? This does requires a balance. We know that card readers are low-tech and someone wanting to inflict harm can easily steal a badge and gain access. But, is the device so complex that your staff just won’t get it? Is the technology too new? Too new that it hasn’t been tried and tested?
(2) Where is the device placed? Is it underneath a black piece of glass, hidden from view? Is it on the left side of the hallway when someone is expecting to see it on the right? Check out some integration techniques we’ve seen in an earlier blog post.
Access control systems and security entrances go hand-in-hand in preventing tailgating and unauthorized entry. We encourage you to think hard about which access control device will function appropriately to meet your organization’s unique security goals.

